FinCEN Advisory on Ransomware
FinCEN Advisory on Ransomware
FinCEN highlighted ransomware attacks as a growing concern for banks and financial institutions in the role they play potentially facilitating ransomware payments.
On October 1, 2020, FinCEN issued an Advisory on Ransomware and the Use of the Financial System to Facilitate Ransom Payments. In the advisory, FinCEN highlighted ransomware attacks as a growing concern for banks and financial institutions in the role they play potentially facilitating ransomware payments. The advisory also explains typical typologies used by cybercriminals to monetize their ransomware activity through financial institutions, money services businesses (MSBs), and the use of convertible virtual currency (CVC), as depicted in Figure 1. We highlight some of the key points from the advisory.
FIGURE 1.
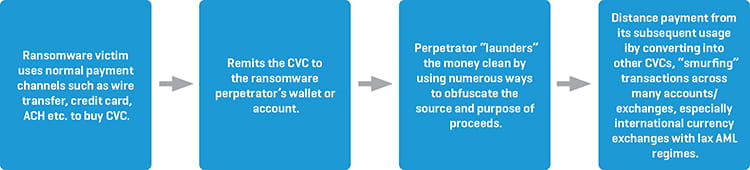
Ransomware Typologies
Certain industries and entities are more prone to cyber-attacks. These include government entities, financial institutions, and organizations that have more limited information technology (IT) infrastructure and incident response capabilities. The attacks may employ various methods to entice victims to download a file with malicious content or redirect them to a malicious website. Clicking on such links will typically allow the malware to exploit vulnerabilities within the victim’s network. The FinCEN guidance further lists different ransomware schemes and operations and encourages financial institutions to be alert for the different ransomware red flags.
Financial Red Flag Indicators of Ransomware and Associated Payments
FinCEN has identified several financial red flag indicators of potential ransomware activity to assist financial institutions in detecting, preventing, and reporting suspicious transactions associated with ransomware activity.
- IT enterprise activity in system log files, network traffic, or file information displays indicators associated with possible ransomware activity or known cyber threat actors / ransomware perpetrators. Malicious cyber activity may be evident.
- When opening a new account or during other interactions with the financial institution, a customer provides information that a payment is in response to a ransomware incident.
- A customer’s CVC address, or an address with which a customer transacts, appears on open sources, or commercial or government analyses have linked those addresses to ransomware strains, payments, etc. A transaction occurs between an organization from a higher-risk sector for ransomware (e.g., government, financial, educational, healthcare, etc.) and a digital forensics and incident response (DFIR) company or a cyber insurance company (CIC), especially one known to facilitate ransomware payments. A DFIR or CIC customer receives funds from a customer company and, shortly after receipt of funds, sends equivalent amounts to a CVC exchange.
- A customer shows limited knowledge of CVC yet enquires about or purchases CVC (particularly if in a large amount or rush requests), which may indicate the customer is a victim of ransomware.
- A DFIR, CIC, or other company that has no, or limited, history of CVC transactions sends a large CVC transaction, particularly if outside a company’s normal business practices.
- A customer that has not identified itself to the CVC exchanger, or registered with FinCEN as a money transmitter, appears to be using the liquidity provided by the exchange to execute large numbers of offsetting transactions between various CVCs. This may indicate that the customer is acting as an unregistered MSB.
- A customer uses a CVC exchanger or foreign-located MSB in a high-risk jurisdiction lacking, or known to have inadequate, anti-money laundering/combating the financing of terrorism (AML/CFT) regulations for CVC entities.
- A customer initiates multiple rapid trades between multiple CVCs, especially anonymity enhanced coins (AECs), with no apparent related purpose, which may be indicative of attempts to break the chain of custody on the respective blockchains or further obfuscate the transaction.
Financial Institutions Obligations to File Suspicious Activity Reports (SARs)
Financial institutions should determine if filing a SAR is required or appropriate when dealing with an incident of ransomware when the financial institution itself has been a victim of a ransomware attack. Reportable activity can involve payments related to criminal activity like extortion and unauthorized access that damage, disable, or otherwise affect critical systems. When filing a SAR, a financial institution should provide all pertinent available information on the event, including cyber-related information and technical indicators, in the SAR form and narrative.
The advisory lists valuable cyber indicators for law enforcement investigations for ransomware, including email addresses, internet protocol (IP) addresses, login information with location and timestamps, virtual currency wallet addresses, mobile device information (such as device international mobile equipment identity (IMEI) numbers), malware hashes, malicious domains, and descriptions and timing of suspicious electronic communications.
FinCEN has requested that financial institutions include the key term: “CYBER-FIN-2020-A006” in SAR field 2 (Filing Institution Note to FinCEN) and the narrative to indicate the suspicious activity is ransomware-related activity. Financial institutions should also select SAR field 42 (Cyber event) as the associated suspicious activity type, as well as select SAR field 42z (Cyber event - Other) while including “ransomware” as keywords in SAR field 42z, to indicate the suspicious activity being reported is possible ransomware activity.







