What’s on Your (and Your Employee’s) Smartphone?
What’s on Your (and Your Employee’s) Smartphone?
With the proliferation of data circulating among smartphone users, businesses need to implement and proactively manage employee mobile-device policies to ensure that proprietary company information stays protected.
The numbers of technology and smartphone users continues to explode at an unprecedented rate. As shown in Figure 1, key statistics indicate the enormous volume of users.
What’s on your smartphone?
Well, just about everything! Mobile devices (i.e. smartphones), as noted by Chief Justice John Roberts in the Riley v. California matter, are “such a pervasive and insistent
part of daily life that the proverbial visitor from Mars might conclude they were an important feature of human anatomy.”
Figure 1. Digital Around the World in 2018
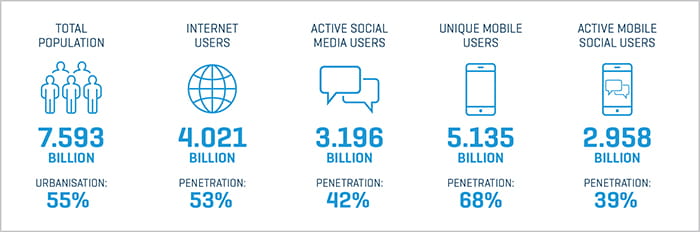
Image source: HootSuite. Data sources: Population: United Nations; U.S. Census Bureau. Internet: InternetWorldStats; ITU; Eurostat; InternetLiveStats; CIA World Factbook; mideastmedia.org; Facebook; Government Officials; Regulatory Authorities; Reputable Media. Social Media and Mobile Social Media: Facebook; Tencent; VKonTakte; Kakao; Naver; Ding; Techrasa; SimilarWeb; Kepios Analysis. Mobile: GSMA Intelligence; Google; Ericsson; Kepios Analysis. Note: Penetration figures are for total population (all ages).
Types of data found on smartphones include:
- Calls, text messages, logs, and contacts – often with associated personally identifiable information
- Calendars, schedules, geolocation, and GPS history
- “To Do” lists and tasks
- Photos and videos (including time stamps and locations)
- Internet history and social media
- Email (personal and/or company)
- Third-party applications (personal and/or company)
This data, from the eyes of a digital forensics expert, might be described as likely recoverable and potentially evidence. It is similar to any other type of electronically stored information (ESI), whereby:
- Federal rules including discoverability, litigation holds, and preservation requirements apply
- It is viewed and treated as communications
- It is often relevant, unique, and extremely compelling
- It can change the course of an investigation or legal matter
In fact, two recent amendments to the Federal Rules of Evidence address the increasing prevalence ESI, allowing for the self-authentication of electronic evidence in legal proceedings. Rule 902(13) covers records “generated by an electronic process or system that produces an accurate result such as a system registry report showing that a device was connected to a computer, or showing how software obtains GPS coordinates.” Rule 902(14) establishes that electronic data recovered “by a process of identification” is to be self-authenticating, thereby not routinely necessitating the trial testimony of a forensic or technical expert where best practices are employed, as certified through a written affidavit by a “qualified person” that complies with the certification requirements of Rule 902(11) or (12).
The Digital Trail of Evidence
We know that smartphones leave behind an indisputable digital trail that can lead to many types of security risks. Most employers have surrendered to the pressures of the marketplace and are allowing employees to BYOD (bring your own device), which connects to their account and company applications, as well as to their personal iCloud or Dropbox accounts and much, much more. Issues related to device control and company trade information, including trade secret misappropriation, abide.
Users admit that:
- 84% store sensitive data on their mobile devices
- 55% send work emails and company data on their personal email accounts using a mobile device
- 89% have mobile devices connected to company networks, and that there will be times where these devices will be used outside the control of a company’s IT security controls
What Actions Should Companies Take?
Should individuals (and companies) be concerned? What needs to be done to address this proliferation of technology, smartphones, and associated data to counter the risks?
For starters, companies need to have in place basic protections in terms of agreements and policies with employees. These protections include the following:
- Confidentiality and nondisclosure agreements that describe and establish what is considered confidential and/or proprietary information
- Employee handbooks outlining an employee’s fiduciary duties to the company
- Acceptable usage practices that establish what users should and should not do with the IT assets at their disposal and associated data
- Ongoing and periodic training, awareness, and monitoring practices that provide relevant information about changes in the technological environment, privacy and social media use policies, and verify that the procedures and data entrusted to employees is being properly handled, employing the practice of “Trust, then verify”
- Incorporate well-defined noncompete contracts and terms to help protect internal and employee information from poachers of trade secrets and other items
In addition, companies need to proactively manage BYOD policies in a systematic manner, with best practices, such as:
- Vigorously take advantage of controls that require strong passwords/passcodes, two-factor authentication, and encryption
- Use a mobile device management suite or remote access solution that identifies, controls, and potentially requires consent when the solutions are installed
- Conduct routine and ad-hoc security checks (focus and protecting high-value assets)
- Identify up-front procedures regarding employee changes in position, department, and potential departure, and consider how business-related data will be handled
- Provide guidance and steps regarding changes to or the discarding of smartphones. Data “wiped” does not always mean that data is unrecoverable
The proliferation of smartphone usage and the availability of data is at an all-time high. The practice of BYOD is now common at many companies, providing both risks and opportunities. When developing an ESI strategy with applications and associated policy and usage guidelines, companies should keep in mind that data from employees’ smartphones likely can be recovered and potentially used as evidence.
Authored by:
Chad Gough, CISSP
Founder – 4Discovery, LLC
+1.312.924.5761
chad@4discovery.com
This article was adapted from the CLE presentation “Mobile Discovery: Outsmarting the Smartphone.”
Chad Gough is the founding partner of 4Discovery and has managed aspects of computer forensics and electronic discovery, including expert witness testimony, for more than 20 years. He is a frequent speaker on these topics and currently teaches a course on computer security. 4Discovery specializes on investigations that involve: trade secrets theft, employee misconduct, corporate espionage, insider trading, fraud and/or embezzlement and software piracy.
